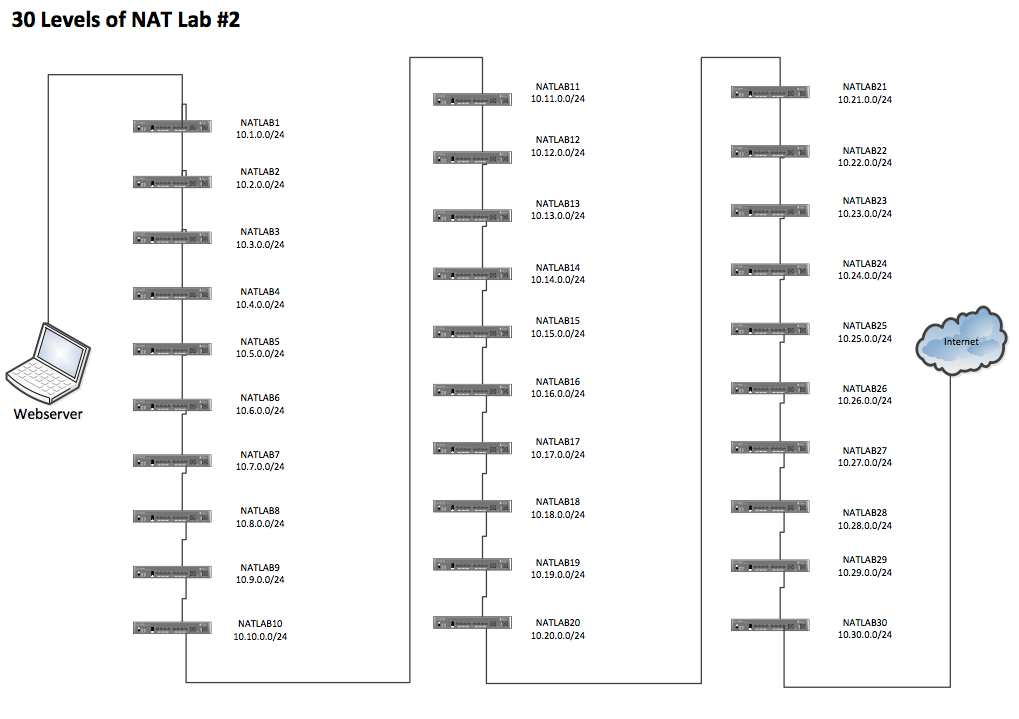
Well, I had the chance again to play with lots of Firewalls, so I did. A customer had ordered > than 30 SRX100s for clustered branch deployments so I took the opportunity to ask for permission to pull 30 of them out of boxes and reproduce my 30 levels of NAT lab. It\'s never the same doing it alone so I put the word out to some nerd mates and got Mr Aijay Adams (@aijayadams) and Master Mitch Hewes (@mitcdh) to tag along and enjoy the extremly draining NAT filled day. The day included unboxing, \'racking\' and cabling, configuring and then packing it all up. It was a long day, especially since we tried to get routing instances to NAT 10 times on each SRX ... We were not successful, it seems LT interfaces are not NAT friendly (which is good, cause it\'s stupid and I hate NAT). Here is the logical layout:
Of course, for good measure, a quick video of our fun 🙂
So we set the SRX\'s up identically to the PIX501s 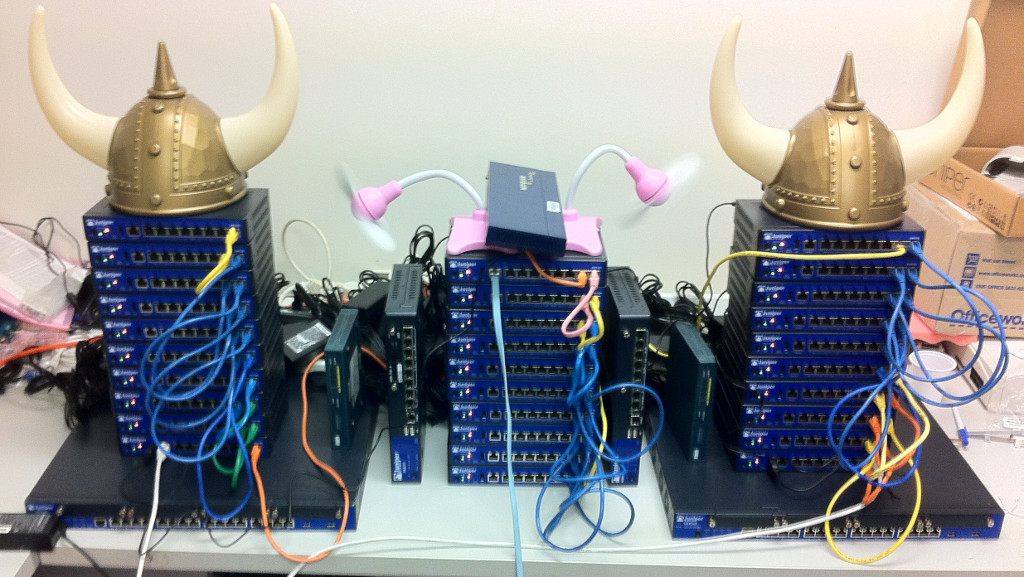 (not as neat - Time didn\'t allow that :))
(not as neat - Time didn\'t allow that :))
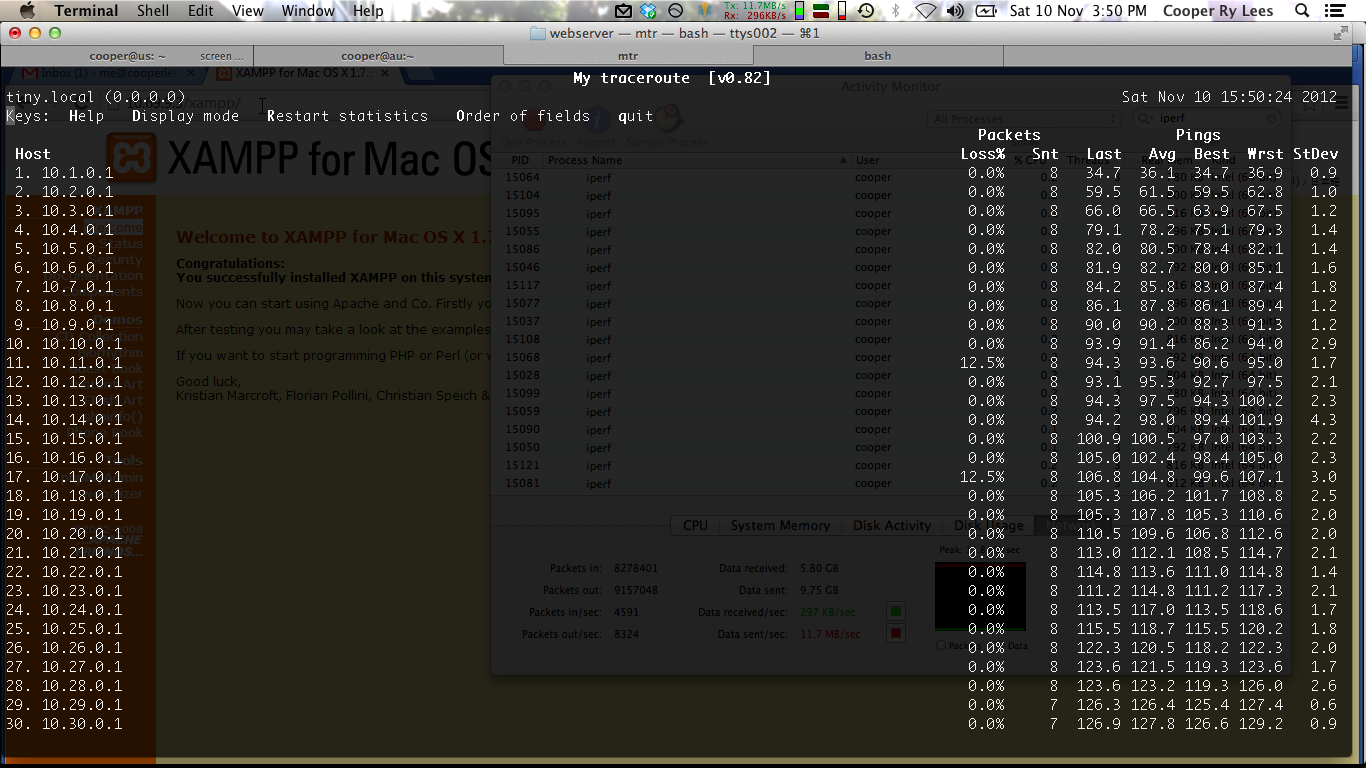
The results were similiar to the Cisco\'s latency wise, but throughput was what I really expected originally (before I did the Cisco NAT LAB), the SRX100s were able to achieve the full 100mbit through the 30 levels of NAT. After getting the same level of NAT achieved as the Cisco lab we set out to better it, by using routing-instances and lt interfaces, but it seems NAT from an lt-* interfaces is not supported in Junos (all be it a stupid requirement, still handy to know). If someone can see what I did wrong in the config below I would love to know. We had to call it quits after many hours trying to get the routing-instances to work, but we were so close! P.S. I know I could of used all the physicals, I did not have enough patch cables ! Here is a screenshot of a traceroute of out NATHELL With no throughput: 

 ## Nerdy Setup Details
## Nerdy Setup Details
1 NAT per Box Config:
set system host-name NATLAB0
set system domain-name cooperlees.com
set system root-authentication encrypted-password lab123
set system name-server 192.168.83.6
set system name-server 192.168.83.5
set system name-server 8.8.8.8
set system services ssh
set system services dhcp pool 10.0.0.0/24 address-range low 10.0.0.10
set system services dhcp pool 10.0.0.0/24 address-range high 10.0.0.100
set system services dhcp pool 10.0.0.0/24 name-server 192.168.83.5
set system services dhcp pool 10.0.0.0/24 name-server 192.168.83.6
set system services dhcp pool 10.0.0.0/24 name-server 8.8.8.8
set system services dhcp pool 10.0.0.0/24 domain-search cooperlees.com
set system services dhcp pool 10.0.0.0/24 router 10.0.0.1
set interfaces interface-range ACCESS member-range fe-0/0/0 to fe-0/0/6
set interfaces interface-range ACCESS unit 0 family ethernet-switching
set interfaces fe-0/0/7 unit 0 family inet address 10.1.0.2/24
set interfaces vlan unit 0 family inet address 10.0.0.1/24
set routing-options static route 0.0.0.0/0 next-hop 10.1.0.1
set security nat source rule-set Outbound-NAT from zone NATHELL
set security nat source rule-set Outbound-NAT to zone LESSNAT
set security nat source rule-set Outbound-NAT rule egress-int-bitch match destination-address 0.0.0.0/0
set security nat source rule-set Outbound-NAT rule egress-int-bitch then source-nat interface
set security nat destination pool WEBSERVER address 10.0.0.2/32
set security nat destination rule-set Internet-PAT from zone LESSNAT
set security nat destination rule-set Internet-PAT rule WEBSERVER-PAT match destination-address 10.1.0.2/32
set security nat destination rule-set Internet-PAT rule WEBSERVER-PAT match destination-port 80
set security nat destination rule-set Internet-PAT rule WEBSERVER-PAT then destination-nat pool WEBSERVER
set security policies from-zone NATHELL to-zone LESSNAT policy allow-all-bitch match source-address any
set security policies from-zone NATHELL to-zone LESSNAT policy allow-all-bitch match destination-address any
set security policies from-zone NATHELL to-zone LESSNAT policy allow-all-bitch match application any
set security policies from-zone NATHELL to-zone LESSNAT policy allow-all-bitch then permit
set security policies from-zone NATHELL to-zone LESSNAT policy allow-all-bitch then log session-init
set security zones security-zone NATHELL host-inbound-traffic system-services all
set security zones security-zone NATHELL host-inbound-traffic protocols all
set security zones security-zone NATHELL interfaces vlan.0
set security zones security-zone LESSNAT host-inbound-traffic system-services all
set security zones security-zone LESSNAT host-inbound-traffic protocols all
set security zones security-zone LESSNAT interfaces fe-0/0/7.0
set vlans default l3-interface vlan.0
10 NATs per Box Attempt:
This config did not work with the NAT\'ing between RI\'s over the LT interfaces. The goal was: 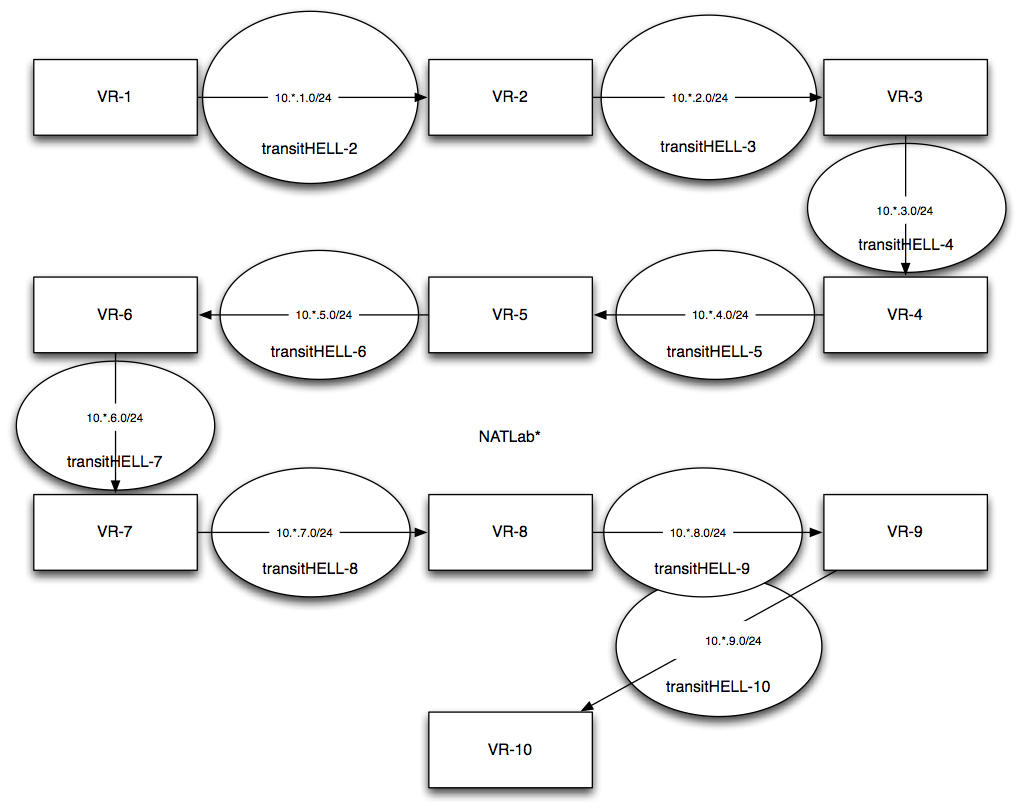
set system host-name NATLAB1
set system domain-name cooperlees.com
set system root-authentication encrypted-password $1$fU1Lb028$c/LeEFORggONDEgKovRyj.
set system name-server 192.168.83.6
set system name-server 192.168.83.5
set system name-server 8.8.8.8
set system services ssh
set system services dhcp pool 10.1.0.0/24 address-range low 10.1.0.10
set system services dhcp pool 10.1.0.0/24 address-range high 10.1.0.100
set system services dhcp pool 10.1.0.0/24 name-server 192.168.83.5
set system services dhcp pool 10.1.0.0/24 name-server 192.168.83.6
set system services dhcp pool 10.1.0.0/24 name-server 8.8.8.8
set system services dhcp pool 10.1.0.0/24 domain-search cooperlees.com
set system services dhcp pool 10.1.0.0/24 router 10.1.0.1
set interfaces interface-range ACCESS member-range fe-0/0/0 to fe-0/0/6
set interfaces interface-range ACCESS unit 0 family ethernet-switching
set interfaces lt-0/0/0 unit 0 encapsulation ethernet
set interfaces lt-0/0/0 unit 0 peer-unit 1
set interfaces lt-0/0/0 unit 0 family inet address 10.1.1.1/24
set interfaces lt-0/0/0 unit 1 encapsulation ethernet
set interfaces lt-0/0/0 unit 1 peer-unit 0
set interfaces lt-0/0/0 unit 1 family inet address 10.1.1.2/24
set interfaces lt-0/0/0 unit 2 encapsulation ethernet
set interfaces lt-0/0/0 unit 2 peer-unit 3
set interfaces lt-0/0/0 unit 2 family inet address 10.1.2.1/24
set interfaces lt-0/0/0 unit 3 encapsulation ethernet
set interfaces lt-0/0/0 unit 3 peer-unit 2
set interfaces lt-0/0/0 unit 3 family inet address 10.1.2.2/24
set interfaces lt-0/0/0 unit 4 encapsulation ethernet
set interfaces lt-0/0/0 unit 4 peer-unit 5
set interfaces lt-0/0/0 unit 4 family inet address 10.1.3.1/24
set interfaces lt-0/0/0 unit 5 encapsulation ethernet
set interfaces lt-0/0/0 unit 5 peer-unit 4
set interfaces lt-0/0/0 unit 5 family inet address 10.1.3.2/24
set interfaces lt-0/0/0 unit 6 encapsulation ethernet
set interfaces lt-0/0/0 unit 6 peer-unit 7
set interfaces lt-0/0/0 unit 6 family inet address 10.1.4.1/24
set interfaces lt-0/0/0 unit 7 encapsulation ethernet
set interfaces lt-0/0/0 unit 7 peer-unit 6
set interfaces lt-0/0/0 unit 7 family inet address 10.1.4.2/24
set interfaces lt-0/0/0 unit 8 encapsulation ethernet
set interfaces lt-0/0/0 unit 8 peer-unit 9
set interfaces lt-0/0/0 unit 8 family inet address 10.1.5.1/24
set interfaces lt-0/0/0 unit 9 encapsulation ethernet
set interfaces lt-0/0/0 unit 9 peer-unit 8
set interfaces lt-0/0/0 unit 9 family inet address 10.1.5.2/24
set interfaces lt-0/0/0 unit 10 encapsulation ethernet
set interfaces lt-0/0/0 unit 10 peer-unit 11
set interfaces lt-0/0/0 unit 10 family inet address 10.1.6.1/24
set interfaces lt-0/0/0 unit 11 encapsulation ethernet
set interfaces lt-0/0/0 unit 11 peer-unit 10
set interfaces lt-0/0/0 unit 11 family inet address 10.1.6.2/24
set interfaces lt-0/0/0 unit 12 encapsulation ethernet
set interfaces lt-0/0/0 unit 12 peer-unit 13
set interfaces lt-0/0/0 unit 12 family inet address 10.1.7.1/24
set interfaces lt-0/0/0 unit 13 encapsulation ethernet
set interfaces lt-0/0/0 unit 13 peer-unit 12
set interfaces lt-0/0/0 unit 13 family inet address 10.1.7.2/24
set interfaces lt-0/0/0 unit 14 encapsulation ethernet
set interfaces lt-0/0/0 unit 14 peer-unit 15
set interfaces lt-0/0/0 unit 14 family inet address 10.1.8.1/24
set interfaces lt-0/0/0 unit 15 encapsulation ethernet
set interfaces lt-0/0/0 unit 15 peer-unit 14
set interfaces lt-0/0/0 unit 15 family inet address 10.1.8.2/24
set interfaces lt-0/0/0 unit 16 encapsulation ethernet
set interfaces lt-0/0/0 unit 16 peer-unit 17
set interfaces lt-0/0/0 unit 16 family inet address 10.1.9.1/24
set interfaces lt-0/0/0 unit 17 encapsulation ethernet
set interfaces lt-0/0/0 unit 17 peer-unit 16
set interfaces lt-0/0/0 unit 17 family inet address 10.1.9.2/24
set interfaces fe-0/0/7 unit 0 family inet address 10.2.0.2/24
set interfaces vlan unit 0 family inet address 10.1.0.1/24
set routing-options static route 0.0.0.0/0 next-hop 10.2.0.1
set security nat source rule-set Outbound-NAT from interface lt-0/0/0.17
set security nat source rule-set Outbound-NAT to interface fe-0/0/7.0
set security nat source rule-set Outbound-NAT rule egress-int-bitch match destination-address 0.0.0.0/0
set security nat source rule-set Outbound-NAT rule egress-int-bitch then source-nat interface
set security nat source rule-set th3 from zone transitHELL-2
set security nat source rule-set th3 to zone transitHELL-3
set security nat source rule-set th3 rule natAll-1 match destination-address 0.0.0.0/0
set security nat source rule-set th3 rule natAll-1 then source-nat interface
set security nat source rule-set th4 from interface lt-0/0/0.4
set security nat source rule-set th4 to interface lt-0/0/0.5
set security nat source rule-set th4 rule natAll-2 match destination-address 0.0.0.0/0
set security nat source rule-set th4 rule natAll-2 then source-nat interface
set security nat source rule-set th5 from interface lt-0/0/0.6
set security nat source rule-set th5 to interface lt-0/0/0.7
set security nat source rule-set th5 rule natAll-3 match destination-address 0.0.0.0/0
set security nat source rule-set th5 rule natAll-3 then source-nat interface
set security nat source rule-set th6 from interface lt-0/0/0.8
set security nat source rule-set th6 to interface lt-0/0/0.9
set security nat source rule-set th6 rule natAll-4 match destination-address 0.0.0.0/0
set security nat source rule-set th6 rule natAll-4 then source-nat interface
set security nat source rule-set th7 from interface lt-0/0/0.10
set security nat source rule-set th7 to interface lt-0/0/0.11
set security nat source rule-set th7 rule natAll-5 match destination-address 0.0.0.0/0
set security nat source rule-set th7 rule natAll-5 then source-nat interface
set security nat source rule-set th8 from interface lt-0/0/0.12
set security nat source rule-set th8 to interface lt-0/0/0.13
set security nat source rule-set th8 rule natAll-6 match destination-address 0.0.0.0/0
set security nat source rule-set th8 rule natAll-6 then source-nat interface
set security nat source rule-set Inbound-NAT from interface vlan.0
set security nat source rule-set Inbound-NAT to interface lt-0/0/0.0
set security nat source rule-set Inbound-NAT rule natAll-0 match destination-address 0.0.0.0/0
set security nat source rule-set Inbound-NAT rule natAll-0 then source-nat interface
set security nat source rule-set th9 from interface lt-0/0/0.14
set security nat source rule-set th9 to interface lt-0/0/0.15
set security nat source rule-set th9 rule natAll-7 match destination-address 0.0.0.0/0
set security nat source rule-set th9 rule natAll-7 then source-nat interface
set security nat source rule-set th10 from interface lt-0/0/0.16
set security nat source rule-set th10 to interface lt-0/0/0.17
set security nat source rule-set th10 rule natAll-8 match destination-address 0.0.0.0/0
set security nat source rule-set th10 rule natAll-8 then source-nat interface
set security nat destination pool WEBSERVER address 10.1.0.10/32
set security nat destination rule-set Internet-PAT from zone LESSNAT
set security nat destination rule-set Internet-PAT rule WEBSERVER-PAT match destination-address 10.2.0.2/32
set security nat destination rule-set Internet-PAT rule WEBSERVER-PAT match destination-port 80
set security nat destination rule-set Internet-PAT rule WEBSERVER-PAT then destination-nat pool WEBSERVER
set security policies from-zone NATHELL to-zone LESSNAT policy allow-all-bitch match source-address any
set security policies from-zone NATHELL to-zone LESSNAT policy allow-all-bitch match destination-address any
set security policies from-zone NATHELL to-zone LESSNAT policy allow-all-bitch match application any
set security policies from-zone NATHELL to-zone LESSNAT policy allow-all-bitch then permit
set security policies from-zone NATHELL to-zone LESSNAT policy allow-all-bitch then log session-init
set security policies from-zone LESSNAT to-zone NATHELL policy allow-webserver-traffic match source-address any
set security policies from-zone LESSNAT to-zone NATHELL policy allow-webserver-traffic match destination-address any
set security policies from-zone LESSNAT to-zone NATHELL policy allow-webserver-traffic match application junos-icmp-all
set security policies from-zone LESSNAT to-zone NATHELL policy allow-webserver-traffic match application junos-http
set security policies from-zone LESSNAT to-zone NATHELL policy allow-webserver-traffic match application junos-ssh
set security policies from-zone LESSNAT to-zone NATHELL policy allow-webserver-traffic then permit
set security policies from-zone LESSNAT to-zone NATHELL policy allow-webserver-traffic then log session-init
set security policies from-zone NATHELL to-zone transitHELL-2 policy NATHELL-to-th2 match source-address any
set security policies from-zone NATHELL to-zone transitHELL-2 policy NATHELL-to-th2 match destination-address any
set security policies from-zone NATHELL to-zone transitHELL-2 policy NATHELL-to-th2 match application any
set security policies from-zone NATHELL to-zone transitHELL-2 policy NATHELL-to-th2 then permit
set security policies from-zone transitHELL-2 to-zone transitHELL-3 policy allow-transit-2 match source-address any
set security policies from-zone transitHELL-2 to-zone transitHELL-3 policy allow-transit-2 match destination-address any
set security policies from-zone transitHELL-2 to-zone transitHELL-3 policy allow-transit-2 match application any
set security policies from-zone transitHELL-2 to-zone transitHELL-3 policy allow-transit-2 then permit
set security policies from-zone transitHELL-3 to-zone transitHELL-4 policy allow-transit-4 match source-address any
set security policies from-zone transitHELL-3 to-zone transitHELL-4 policy allow-transit-4 match destination-address any
set security policies from-zone transitHELL-3 to-zone transitHELL-4 policy allow-transit-4 match application any
set security policies from-zone transitHELL-3 to-zone transitHELL-4 policy allow-transit-4 then permit
set security policies from-zone transitHELL-4 to-zone transitHELL-5 policy allow-transit-5 match source-address any
set security policies from-zone transitHELL-4 to-zone transitHELL-5 policy allow-transit-5 match destination-address any
set security policies from-zone transitHELL-4 to-zone transitHELL-5 policy allow-transit-5 match application any
set security policies from-zone transitHELL-4 to-zone transitHELL-5 policy allow-transit-5 then permit
set security policies from-zone transitHELL-5 to-zone transitHELL-6 policy allow-transit-6 match source-address any
set security policies from-zone transitHELL-5 to-zone transitHELL-6 policy allow-transit-6 match destination-address any
set security policies from-zone transitHELL-5 to-zone transitHELL-6 policy allow-transit-6 match application any
set security policies from-zone transitHELL-5 to-zone transitHELL-6 policy allow-transit-6 then permit
set security policies from-zone transitHELL-6 to-zone transitHELL-7 policy allow-transit-7 match source-address any
set security policies from-zone transitHELL-6 to-zone transitHELL-7 policy allow-transit-7 match destination-address any
set security policies from-zone transitHELL-6 to-zone transitHELL-7 policy allow-transit-7 match application any
set security policies from-zone transitHELL-6 to-zone transitHELL-7 policy allow-transit-7 then permit
set security policies from-zone transitHELL-7 to-zone transitHELL-8 policy allow-transit-8 match source-address any
set security policies from-zone transitHELL-7 to-zone transitHELL-8 policy allow-transit-8 match destination-address any
set security policies from-zone transitHELL-7 to-zone transitHELL-8 policy allow-transit-8 match application any
set security policies from-zone transitHELL-7 to-zone transitHELL-8 policy allow-transit-8 then permit
set security policies from-zone transitHELL-8 to-zone transitHELL-9 policy allow-transit-9 match source-address any
set security policies from-zone transitHELL-8 to-zone transitHELL-9 policy allow-transit-9 match destination-address any
set security policies from-zone transitHELL-8 to-zone transitHELL-9 policy allow-transit-9 match application any
set security policies from-zone transitHELL-8 to-zone transitHELL-9 policy allow-transit-9 then permit
set security policies from-zone transitHELL-9 to-zone LESSNAT policy 9-to-LESSNAT match source-address any
set security policies from-zone transitHELL-9 to-zone LESSNAT policy 9-to-LESSNAT match destination-address any
set security policies from-zone transitHELL-9 to-zone LESSNAT policy 9-to-LESSNAT match application any
set security policies from-zone transitHELL-9 to-zone LESSNAT policy 9-to-LESSNAT then permit
set security policies default-policy permit-all
set security zones security-zone NATHELL host-inbound-traffic system-services all
set security zones security-zone NATHELL host-inbound-traffic protocols all
set security zones security-zone NATHELL interfaces vlan.0
set security zones security-zone NATHELL interfaces lt-0/0/0.0
set security zones security-zone LESSNAT host-inbound-traffic system-services all
set security zones security-zone LESSNAT host-inbound-traffic protocols all
set security zones security-zone LESSNAT interfaces fe-0/0/7.0
set security zones security-zone LESSNAT interfaces lt-0/0/0.17
set security zones security-zone transitHELL-2 host-inbound-traffic system-services all
set security zones security-zone transitHELL-2 host-inbound-traffic protocols all
set security zones security-zone transitHELL-2 interfaces lt-0/0/0.1
set security zones security-zone transitHELL-2 interfaces lt-0/0/0.2
set security zones security-zone transitHELL-3 host-inbound-traffic system-services all
set security zones security-zone transitHELL-3 host-inbound-traffic protocols all
set security zones security-zone transitHELL-3 interfaces lt-0/0/0.3
set security zones security-zone transitHELL-3 interfaces lt-0/0/0.4
set security zones security-zone transitHELL-4 host-inbound-traffic system-services all
set security zones security-zone transitHELL-4 host-inbound-traffic protocols all
set security zones security-zone transitHELL-4 interfaces lt-0/0/0.5
set security zones security-zone transitHELL-4 interfaces lt-0/0/0.6
set security zones security-zone transitHELL-5 host-inbound-traffic system-services all
set security zones security-zone transitHELL-5 host-inbound-traffic protocols all
set security zones security-zone transitHELL-5 interfaces lt-0/0/0.7
set security zones security-zone transitHELL-5 interfaces lt-0/0/0.8
set security zones security-zone transitHELL-6 host-inbound-traffic system-services all
set security zones security-zone transitHELL-6 host-inbound-traffic protocols all
set security zones security-zone transitHELL-6 interfaces lt-0/0/0.9
set security zones security-zone transitHELL-6 interfaces lt-0/0/0.10
set security zones security-zone transitHELL-7 host-inbound-traffic system-services all
set security zones security-zone transitHELL-7 host-inbound-traffic protocols all
set security zones security-zone transitHELL-7 interfaces lt-0/0/0.11
set security zones security-zone transitHELL-7 interfaces lt-0/0/0.12
set security zones security-zone transitHELL-8 host-inbound-traffic system-services all
set security zones security-zone transitHELL-8 host-inbound-traffic protocols all
set security zones security-zone transitHELL-8 interfaces lt-0/0/0.13
set security zones security-zone transitHELL-8 interfaces lt-0/0/0.14
set security zones security-zone transitHELL-9 host-inbound-traffic system-services all
set security zones security-zone transitHELL-9 host-inbound-traffic protocols all
set security zones security-zone transitHELL-9 interfaces lt-0/0/0.15
set security zones security-zone transitHELL-9 interfaces lt-0/0/0.16
set routing-instances 1 instance-type virtual-router
set routing-instances 1 interface lt-0/0/0.0
set routing-instances 1 interface vlan.0
set routing-instances 1 routing-options static route 0.0.0.0/0 next-hop 10.1.1.2
set routing-instances 10 instance-type virtual-router
set routing-instances 10 interface lt-0/0/0.17
set routing-instances 10 interface fe-0/0/7.0
set routing-instances 10 routing-options static route 0.0.0.0/0 next-hop 10.2.0.1
set routing-instances 2 instance-type virtual-router
set routing-instances 2 interface lt-0/0/0.1
set routing-instances 2 interface lt-0/0/0.2
set routing-instances 2 routing-options static route 0.0.0.0/0 next-hop 10.1.2.2
set routing-instances 3 instance-type virtual-router
set routing-instances 3 interface lt-0/0/0.3
set routing-instances 3 interface lt-0/0/0.4
set routing-instances 3 routing-options static route 0.0.0.0/0 next-hop 10.1.3.2
set routing-instances 4 instance-type virtual-router
set routing-instances 4 interface lt-0/0/0.5
set routing-instances 4 interface lt-0/0/0.6
set routing-instances 4 routing-options static route 0.0.0.0/0 next-hop 10.1.4.2
set routing-instances 5 instance-type virtual-router
set routing-instances 5 interface lt-0/0/0.7
set routing-instances 5 interface lt-0/0/0.8
set routing-instances 5 routing-options static route 0.0.0.0/0 next-hop 10.1.5.2
set routing-instances 6 instance-type virtual-router
set routing-instances 6 interface lt-0/0/0.9
set routing-instances 6 interface lt-0/0/0.10
set routing-instances 6 routing-options static route 0.0.0.0/0 next-hop 10.1.6.2
set routing-instances 7 instance-type virtual-router
set routing-instances 7 interface lt-0/0/0.11
set routing-instances 7 interface lt-0/0/0.12
set routing-instances 7 routing-options static route 0.0.0.0/0 next-hop 10.1.7.2
set routing-instances 8 instance-type virtual-router
set routing-instances 8 interface lt-0/0/0.13
set routing-instances 8 interface lt-0/0/0.14
set routing-instances 8 routing-options static route 0.0.0.0/0 next-hop 10.1.8.2
set routing-instances 9 instance-type virtual-router
set routing-instances 9 interface lt-0/0/0.15
set routing-instances 9 interface lt-0/0/0.16
set routing-instances 9 routing-options static route 0.0.0.0/0 next-hop 10.1.9.2
set vlans default l3-interface vlan.0Conf Generation Shell Script:
#!/bin/bash
for i in $(seq 0 30)
do
echo -n "Doing $i ..."
N1=$(expr $i + 1)
cp template.txt $i.conf # Replace N1
sed -i s/#N1/$N1/g $i.conf # Replace N
sed -i s/#N/$i/g $i.conf
echo done
doneUntil we NAT again ...
